Organizations are increasingly turning to cloud computing for its many benefits. Whether it’s the flexibility of remote work or the efficiency gains of cloud solutions, the advantages are undeniable. However, with this transition comes a critical challenge – ensuring data security in the cloud. Many companies offer fortified connectivity, and offer solutions to the unique risks associated with cloud computing and have developed robust approaches to address these concerns.
The evolution of cloud computing is transforming how organizations operate. However, with these technological advancements comes a pressing need for enhanced security measures. RESKOM delves into the dynamic landscape of cloud computing security, exploring the evolution of threats and the imperative to adapt security strategies to meet the challenges of today and tomorrow.
Understanding Cloud Data Security
The Shifting Landscape
Cybersecurity emerges as a top priority for companies undergoing digital transformation. The rise of remote and hybrid workplaces requires a reevaluation of cybersecurity strategies, with cloud computing emerging as a foundational technology. However, many cloud solutions lack built-in security features, highlighting the urgency for a dedicated focus on data security.
Defining Cloud Data Security
Cloud data security involves a combination of technology solutions, policies, and procedures implemented by enterprises to protect cloud-based applications, systems, and associated data and user access. Adhering to the core principles of confidentiality, integrity, and availability (CIA triad), data security in the cloud spans various models and categories, requiring a comprehensive approach throughout the data lifecycle.
Identifying Risks
While the advantages of cloud computing are substantial, organizations face inherent risks. Cyberattacks and data breaches loom large, with statistics revealing alarming numbers. Regulatory noncompliance, data loss, loss of customer trust, business interruption, and financial losses pose significant challenges. Many companies recognize the urgency of addressing these risks through a proactive and strategic approach.
Mitigating Risks
Navigating the cybersecurity landscape in the cloud era requires a comprehensive understanding of the risks involved. RESKOM sheds light on common cloud-related risks, such as regulatory noncompliance, data loss, and business interruption. Furthermore, it presents proactive solutions, including continuous monitoring, encryption, and adherence to compliance standards, to mitigate these risks effectively.
Integration and Data Security
To safeguard data, Many companies offer state-of-the-art security measures, especially during data integration processes. Data integration, a complex and continuous task, is simplified through the use of data ingestion tools. These tools not only facilitate cleansing, profiling, and migration but also embed security measures at each step. Continuous monitoring, encryption, and secure storage protocols are among the common safeguards we recommend.
Key Questions for Data Security Strategy
To guide organizations in their data security strategy, we propose critical questions:
- Ownership of Data Security/Compliance Program: Determine the responsible entity and allocate resources accordingly.
- Incident Response Plan: Chart out all possible scenarios in case of a security incident or data breach and establish a comprehensive response plan.
- Adaptability to Emerging Threats: Outline the frequency and methods for updating security procedures to address existing and emerging threats.
Planning Recommendations Cloud Security
Choosing the Right Integration Tool
When transitioning data to the cloud, selecting the right data integration tool is vital. We emphasize the efficiency gained by automating sub-processes compared to labor-intensive hand-coding. Integration tools not only streamline the migration process but also serve as a shield against security threats during integration.
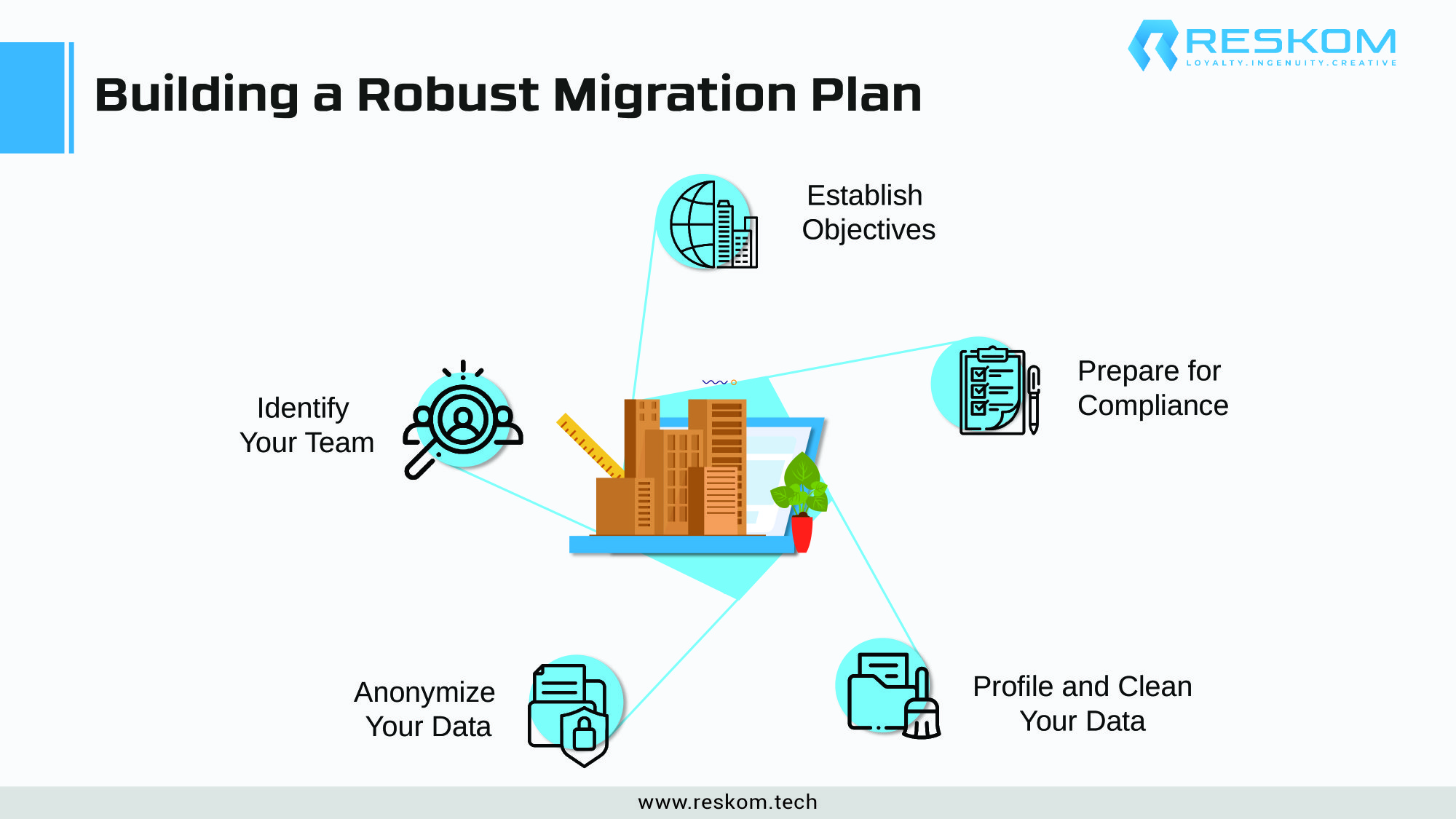
Building a Robust Migration Plan
As organizations embark on data migration, RESKOM advises a structured approach
- Identify Your Team: Assemble a diverse team comprising data architects, scientists, protection experts, business leaders, and project managers.
- Establish Objectives: Align team members by setting ambitious yet realistic goals for the integration process.
- Prepare for Compliance: Stay vigilant on regulatory standards from the outset to ensure a seamless compliance journey.
- Profile and Clean Your Data: Organize and clean data meticulously, unifying diverse data types and resolving errors, inconsistencies, and anomalies.
- Anonymize Your Data: Enhance security and privacy by encrypting or removing personally identifiable information from the data.
RESKOM's Data Governance Principles for the Cloud
A robust data governance framework is the cornerstone of effective cloud data security. RESKOM outlines its data governance principles, emphasizing the critical role of confidentiality, integrity, and availability in safeguarding data. Understanding these principles is important for organizations seeking to fortify their cloud connectivity and uphold the highest standards of data security.
Integration Tools
Integration tools play a vital role in ensuring data security during the migration to the cloud. RESKOM explores the significance of these tools, making it clear how they streamline the integration process, automate sub-processes, and serve as a shield against potential security threats. The advantages of integration tools reveal why they are a fundamental component of RESKOM’s fortified connectivity approach.
Conclusion
Data security is non-negotiable. RESKOM’s fortified connectivity approach offers a comprehensive solution to the unique challenges posed by the cloud. By integrating state-of-the-art security measures, automation, and compliance considerations, RESKOM empowers organizations to confidently navigate their cloud integration journey. As businesses evolve, RESKOM stands at the forefront, ensuring that the advantages of the cloud are harnessed securely and responsibly. The future of cloud computing is exciting, and with RESKOM’s approach, it’s also exceptionally secure.
With RESKOM’s approach lies a commitment to providing a comprehensive shield against the evolving threats inherent in the cloud environment. From robust encryption protocols to advanced automation, we safeguard data from unauthorized access and manipulation. Contact us today for the best solutions!


